During India's Operation Sindoor, launched in May 2025, while ground battles paused, Pakistani hackers escalated cyber attacks on crucial Indian infrastructure. India's response to the terrorist assault in Pahalgam in April 2025, which took the lives of 26 civilians, involved missile strikes on nine terror bases in Pakistan and its occupied territories on May 7. In retaliation, Pakistan targeted key Indian institutions through cyber warfare, utilizing phishing emails to spread malware.
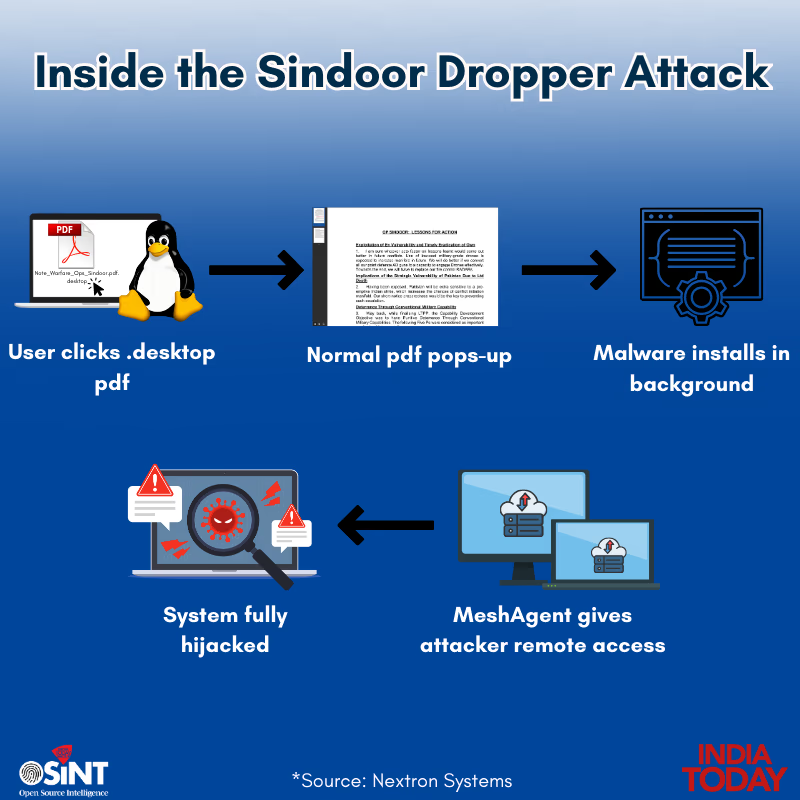
Their deceptive email bore an attachment titled 'Ops Sindoor Lessons For Action', purporting to offer sensitive information on improving defense systems against drone attacks, enticing users to open it. However, the PDF triggered a background process unleashing a malicious code assault on the computer. According to Nextron Systems, the cybersecurity firm, this attack was linked to hackers from APT36 (Transparent Tribe), a group notorious for employing similar tactics.
Source: aajtak
Modus Operandi of the Attack
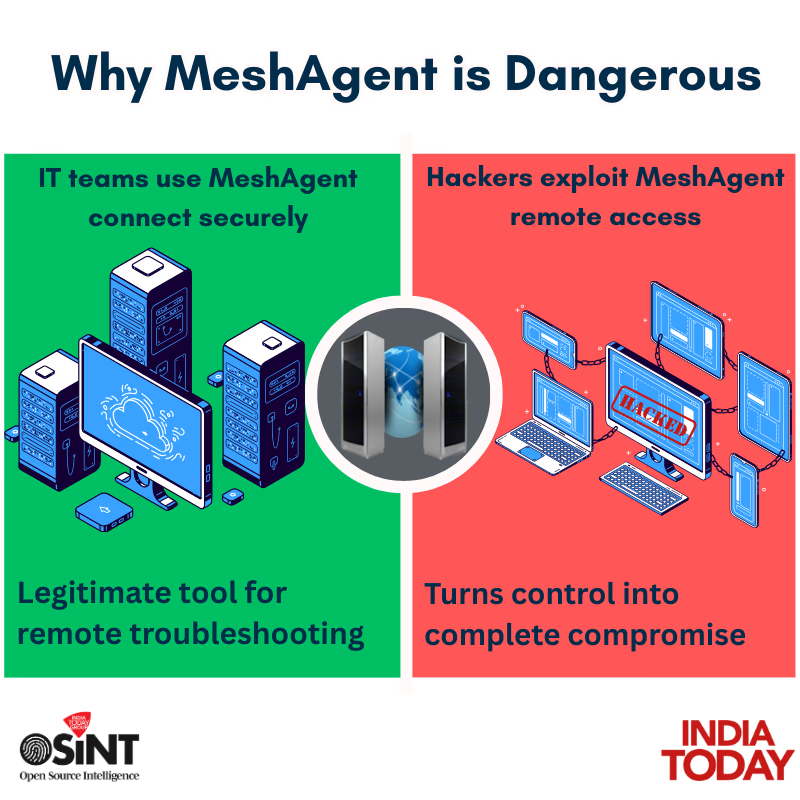
Hackers deployed a PDF named 'Note_Warfare_Ops_Sindoor.pdf.desktop' under the guise of containing secret details of Operation Sindoor. Opening it launched a decoy PDF with trivial content while an infection chain ran in the background, unknowingly installing malicious software on users' systems. This gave hackers complete control, allowing file theft, activity monitoring, and data exports. Notably, they repurposed the legitimate remote control tool MeshAgent for criminal use, enabling remote device control.
Defense Systems As Target
The attack was crafted to exploit Linux-based systems through .desktop files. The defense ministry's Maya OS, an Ubuntu Linux derivative developed by the Defense Research and Development Organization (DRDO) by late 2023, came under threat. In September 2024, a directive from the Controller General of Defense Accounts instructed ministry officials to use only Maya OS/Ubuntu on internet-connected computers.
Source: aajtak
Gradually adopted by the army, navy, and air force, reports reveal over 1,000 cyber attacks on India during Operation Sindoor, 75% of which were DDoS assaults targeting government entities. These strikes impacted ports, airports, power grids, railways, airlines, BSNL, UPI, stock exchanges, and defense PSUs. Alongside Pakistan, groups from Turkey, Bangladesh, Malaysia, Indonesia, and China-supported entities participated. However, many claims were exaggerated, stemming from past data leaks or website defacement incidents.
Ongoing Security Challenges
To safeguard sensitive operations, national security departments employ 'air gap' technology, isolating internet-connected systems from offline ones. Nonetheless, seemingly minor files can become vital to adversaries if they reach internet-connected devices. Cyber experts assert this attack indicates a new phase in India-Pakistan's cyber conflict, with digital infrastructure weaponized. While the government has issued alerts to strengthen cybersecurity, the threat of future attacks looms.




