The mParivahan online vehicle service app, primarily used for e-challan management, is under the spotlight these days. The scam was exposed when a Mumbai professional's funds vanished through a fake version of the mParivahan app, and he shared his ordeal on platform X.
This isn't an isolated case, nor is it the only government app that cybercriminals are copying. Numerous financial loss incidents related to fake government apps have surfaced. To delve deeper, India Today's Open Source Intelligence (OSINT) team investigated the dangerous APK (Android Package Kit) file tricking users and conducted a malware analysis.
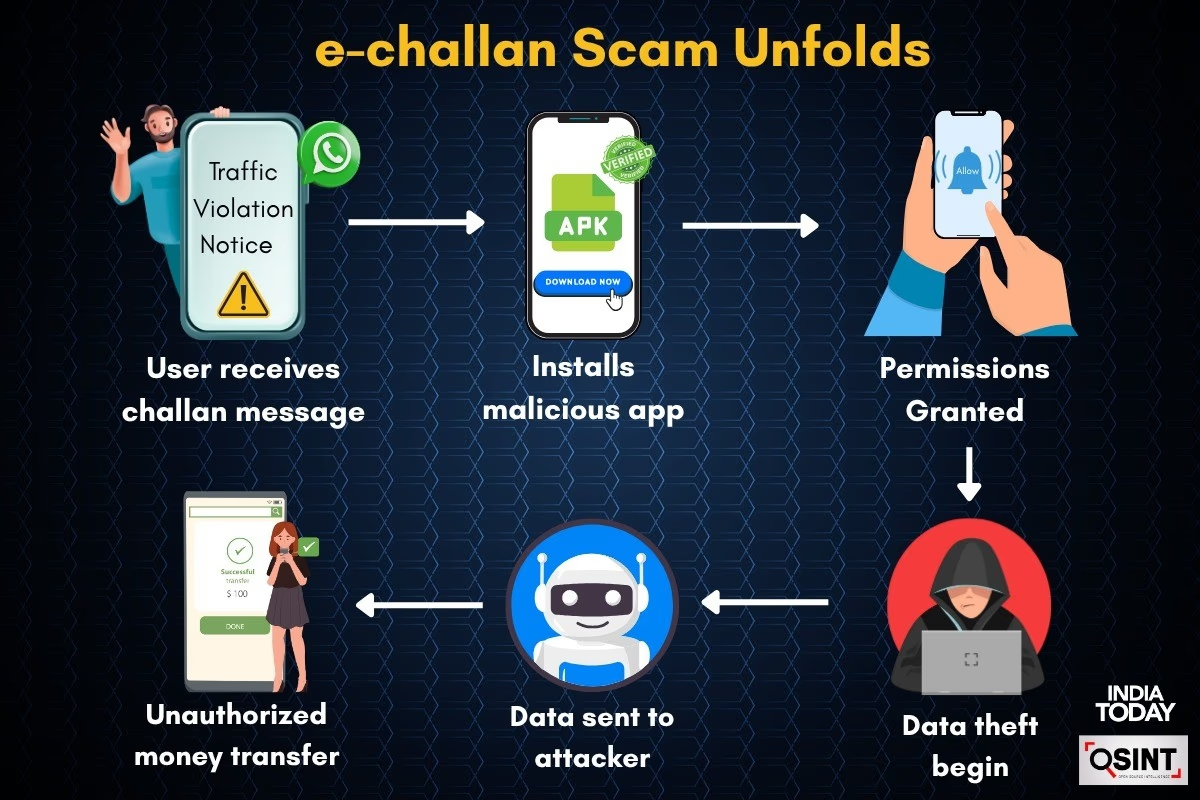
The Scamming Technique
It was uncovered how the scam begins with a WhatsApp message from an Indian number containing a fake APK file and a convincing message with the victim's vehicle number. Once you install it, the app requests access to your contacts, call logs, and messages, giving hackers full control over your data. Moments later, unauthorized transactions commence without warning or your consent.
Data Theft by Scammers
Once trapped, how does your vital data end up in scammers' hands as if it's no big deal? India Today downloaded the infected app and conducted a thorough malware analysis. The APK file was uploaded to the malware scanning platform, VirusTotal, which flagged it for containing BankBot.FTNA.Gen and RewardSteal trojans. These are designed to steal sensitive user data.
Fake Apps That Mirror the Real
The fake APK file closely resembles the legitimate mParivahan app with minor tweaks, deceiving you into allowing it access to phone functions like calls and SMS. Behind the scenes, it siphons off your personal data and sends it to scammers via encrypted Telegram bots.
Source: aajtak
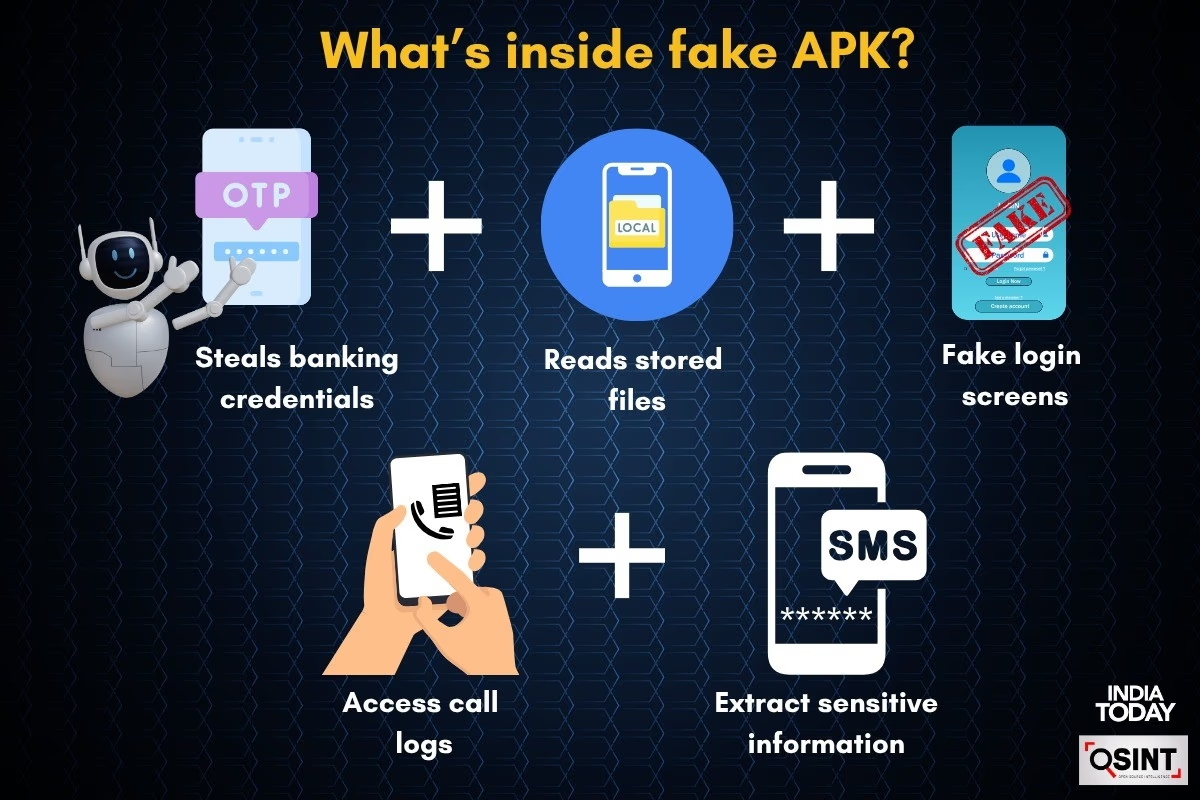
In a previous report, India Today unraveled a ‘Vahan Transport’ APK that intercepted OTPs to carry out fake e-commerce transactions. However, this new clone poses a heightened threat. It aims to steal Aadhaar credentials and banking information. By exploiting device permissions, it gains access to local files and storage, escalating the risk of sensitive data theft significantly.
Once the device is compromised, attackers gain access to SMS, contacts, and storage. The malware creates fake login screens, intercepts OTPs, and extracts crucial documents like Aadhaar. The data is then swiftly sent via encrypted Telegram bots, enabling rapid financial fraud.
Source: aajtak
Attackers can monitor all banking and payment apps installed on the device. The scam's effect isn't limited to the initial victim alone. By hijacking chats and OTPs, cybercriminals can target the victim’s family and contacts, attempting to pilfer their finances too.
This is not just a theoretical threat. A recent case in Bengaluru saw both a victim and his wife facing attempts for unauthorized transactions. An American mobile security firm, Zimperium, earlier reported similar trends where malware spreads through WhatsApp in the form of APK files masquerading as fake government or banking apps. Once installed, these imitations lure users into divulging their financial and personal information.
Targeting Indian Customers
The zLabs research team discovered around 900 malware samples specifically targeting Indian customers who use net and mobile banking apps. Their analysis revealed shared code structures, user interface elements, and app logos, indicating coordinated efforts by the same threat actor targeting mobile devices running on Android OS. Researchers also found 222 exposed Firebase storage buckets containing 2.5 GB of stolen personal and financial data, highlighting the extensive scale of this threat.




